Antivirus vs. anti-malware, or how to effectively fight online threats
 The multitude of terms related to cybersecurity can be dizzying today. We can find many types of malware and methods to protect against them.
The multitude of terms related to cybersecurity can be dizzying today. We can find many types of malware and methods to protect against them.
Unfortunately, some names are often used incorrectly and some concepts are mixed up, which increases the problems associated with the proper understanding of cybersecurity by non-professionals.
An excellent example is the fairly common lack of distinction between antivirus and anti-malware software. Although both tools – the so-called antivirus and anti-malware – are used to protect our IT resources, they are not identical concepts. Let’s check what makes them different and how effective they are in the face of modern threats. To this end, it is worth reaching into the genesis of cybersecurity and analyzing the most popular current types of IT security threats.
1. The story of a virus
Elk Cloner – this was the name of one of the first computer viruses, recognized as a pioneer of modern cyber threats. It attacked Apple II systems in 1982, permanently forging the concept of a computer virus in IT terminology. The first viruses were not too dangerous for the systems at the time, but they were able to spread quickly and self-replicate. Already in the 1990s, viruses became much more aggressive. Newspaper headlines reported attacks destroying data, slowing down systems, and even registering keystrokes to obtain passwords and logins. The need for a software that would be able to fight the new threat became clear.
The first antivirus programs protected against viruses that were already known; unfortunately, new ones were still being created that they could not cope with. So it was necessary to develop and constantly update virus databases to keep up with cybercriminals. A self-accelerating “arms race” began, because programs developed to resist subsequent viruses forced cybercriminals to modify them or create new ones, which, of course, brought about a response from antivirus manufacturers, etc.
1.1. The evolution of Internet threats
Today, however, computer viruses can be considered more a relic of the past than a real threat. Although they still exist, their effectiveness – and therefore also popularity among hackers – has definitely dropped. In return, a whole spectrum of new threats appeared that are collectively called malware. Its best known varieties include: ransomware, adware, spyware, cryptojacking, and exploit. Typical self-replicating viruses are currently also included in this group. What was once a major threat to IT has become just one of many elements of cybercrime. Therefore, modern malware forces the use of tailored modern security methods – namely anti-malware.
2. The most important contemporary threats to cybersecurity
As mentioned above, the number of types of cyber attacks is huge today. Although each of them carries a threat, some are particularly dangerous and, at the same time, very eagerly used by criminals. Let’s take a closer look at ransomware attacks and the so-called zero-day/zero-hour attacks that exploit newly discovered vulnerabilities in systems.
2.1. Ransomware, namely – pay for your data
Ransomware is malicious software whose purpose is to take control of the data on an infected machine and to demand a ransom to unlock them. Although the first cases of this type of attacks appeared already in the 1990s, ransomware really boomed after 2013, when another greatly popular phenomenon spread, namely bitcoin. Thanks to this virtual currency, ransom transactions have become very difficult to track, making cybercriminals even more insolent.
Ransomware attacks private users, state institutions, and companies, also those international. There are many examples of attacks on the latter. In 2016-2017, the two largest ransomware attacks in history showed that the level of global cybersecurity was far behind criminals. WannaCry, which appeared in Europe in mid-2017, after four days affected 250,000 machines in 116 countries of the world and 150,000 Android devices. In turn, Petya, which a few weeks later hit mainly Ukrainian companies and institutions, quickly spread to other countries, including Poland.
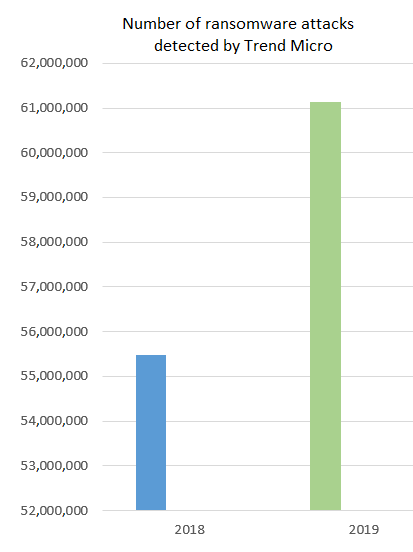
Some time has passed since those events and, as statistics show, the fashion for ransomware is slowly fading away. Even in 2017, as many as 48% of organizations in the United States had to face this type of threat. In the following year, it was only 4%. However, this does not mean that ransomware is leaving the scene. Although attacks do not increase at a fast pace, the targets chosen by cybercriminals are more precise, and the attacks are better carried out. This is demonstrated by, among others, data from the 2019 cybersecurity report published by Trend Micro. According to it, 2019 saw a 10% increase in the number of detected ransomware attacks despite a 57% decrease in the number of new ransomware families compared to 2018.
2.2. Zero-day exploits – better check your updates
According to many security experts, exploits today are one of the key threats to the functioning of IT systems. Exploit is a malicious code that can exploit a vulnerability in the system/application that arose in the programming process to sneak into a computer or server. By opening such open gate in security systems, cybercriminals can freely access the device and install malware to use the hacked system for their own purposes, without the user’s knowledge.
The so-called patches, that is updates prepared and released by the system or application manufacturer, are used to secure such vulnerabilities when discovered. However, what about the period between the discovery of a vulnerability and the release of the update by the manufacturer and installation by the user? Then we can deal with an extremely dangerous phenomenon, which is a zero-day exploit. Protection against such threat is difficult and consists primarily in regularly and frequently checking for system updates and installing them immediately.
Updating applications and systems does not give one hundred percent security guarantee, but an unpatched system is simply asking for trouble, sometimes a really huge one. The data leakage from one of the largest credit bureaus in the US may serve as an example. As a result of not updating the software for previously detected vulnerabilities, data from more than 143 million citizens of this country leaked from the company. This seemingly a small mistake will cost the office up to 700 million dollars. The president of the company said goodbye to the position, and one of the directors ended up in prison for several months.
There are many examples of this type of negligence, unfortunately also in Poland. Looking at the ever-growing number of applications and systems available, the increased activity of cybercriminals exploiting security vulnerabilities seems to be inevitable.
3. Choose antivirus or anti-malware?
Is it necessary to answer this question, and is it possible at all? Looking at the evolution of cyber threats presented above, one thing is certain: tools for protecting network security must keep up with the pace of the development of various types of attacks. Unfortunately, a traditional antivirus software often loses this race, allowing the installation of malware on the terminal device. This does not mean, however, that every antivirus is doomed to failure. Manufacturers of this type of solutions are constantly working on improving their products, trying to make them able to counteract malware as well.
Before making a decision about choosing a particular tool, it should be checked which technologies the given program uses. Is this a standard, somewhat outdated threat detection method based on signature verification, or does the software use modern technology, namely the so-called heuristic analysis. It involves the antivirus program scanning the executable file, in-depth analysis of the program structure, its data and programming logic in search of unusual instructions and fragments of junk code.
In other words:
- An antivirus that only uses signatures is a controller at the air terminal that does not allow only those passengers who are tagged in the information system as dangerous
- The heuristic analysis is a controller that, of course, will not let in those already known and dangerous, but will also exclude from further travel all those behaving suspiciously or trying to smuggle a dangerous load.
Moreover, it is estimated that the average antivirus is now able to capture only about 45% of all malicious traffic that goes through it.
So what strategy should be adopted when choosing cybersecurity software?
Many IT specialists say that the best solution is to install two tools, a reputable antivirus and anti-malware complementing it, which will catch everything that the first one missed. Others, in turn, believe that currently the difference between these tools is symbolic and lies mainly in the naming itself. That is why common sense and choosing the right software for our needs are extremely important.
Before making a decision, it is worth learning the details of individual products and checking what options they have, for example:
- Whether they are able to update the vulnerability base
- What their impact on hardware performance is
- Whether they are able to verify the reputation of websites and block access to dangerous ones
- Whether, apart from informing about detected threats, they also remove them
- Whether they can cope not only with basic threats, but also with unusual ones.
Only with such knowledge base can the right choice be made.
Comprehensive protection for servers
Deep Micro by Trend Micro is a product that provides comprehensive protection for servers (physical, virtual, cloud and container) against all types of cyber threats.
There are three modules which contain a number of tools to protect, among others, against:
- Threats related to outdated software
- All kinds of malware
- Unsolicited actions and changes in the server structure.
Deep Security included in the Atman’s offer is a fully automatic solution working in the background without unnecessary load on the server. Thanks to this, users can be sure to be always equipped with the latest updates for their operating systems and applications (this is provided by the Virtual Patching option that applies virtual patches on security vulnerabilities). The solution package also includes fully professional anti-malware, which is currently one of the most serious tools to fight malware. In turn, tools such as Integrity Monitoring or Application Control provide continuous protection over the server status, monitoring unwanted behaviors, such as attempts to install untrusted applications, suspicious activities, excessive login attempts, etc.
Deep Security definitely cuts off any discussion about the effectiveness of antivirus and anti-malware programs. Deep Security tools combine all the necessary features and functions for effective and reliable protection of server environments.




 The website uses cookies as described in our
The website uses cookies as described in our 